Port Security 1
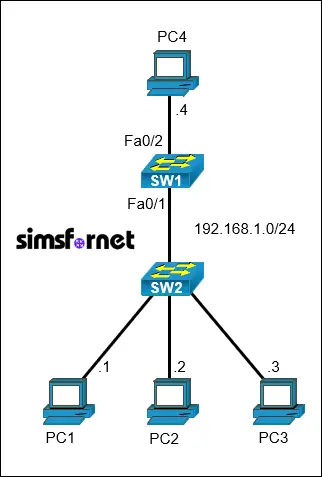
Topology
Tasks:
IP connectivity is established. The SW2 is fully configured and inaccessible. Configure Port Security on SW1 as follows:
- Enable Port Security on SW1's interface connected to SW2.
- Set the maximum number of secure MAC addresses to three.
- Assign the MAC addresses of PC1 and PC2 statically.
- Configure the violation action to block traffic from any additional MAC addresses and log the violation.
- Ping between PC3 and PC4 to ensure they cannot communicate through SW1.
Solution:
Task 1: Enable Port
Security on SW1's interface connected to SW2.
SW1#configure
terminal
SW1(config)#int f0/1
SW1(config-if)#switchport mode access
SW1(config-if)#switchport port-security
switchport mode
access: To enable
port-security on a interface, it is necessary to set the interface as an access
port.
switchport port-security: Enable port-security on the
interface.
Task 2: Set the
maximum number of secure MAC addresses to two.
SW1(config-if)#switchport
port-security maximum 3
This limits the
number of MAC addresses allowed on the interface to 3:
Task 3: Assign the
MAC addresses of PC1 and PC2 statically.
First we need to
find the mac-addresses of PC1 and PC2.
PC1:\>ipconfig /all
---output omitted---
Physical Address...........: 00D0.FF99.B0B7
IPv6 Address...............: ::
IPv4 Address...............: 192.168.1.1
Subnet Mask................: 255.255.255.0
PC2:\>ipconfig /all
---output omitted---
Physical Address...........: 00E0.F9CB.0AB5
IPv6 Address...............: ::
IPv4 Address...............: 192.168.1.2
Subnet Mask................: 255.255.255.0
Now assign these MAC
Addresses statically.
SW1(config-if)#switchport
port-security mac-address 00D0.FF99.B0B7
SW1(config-if)#switchport port-security mac-address 00E0.F9CB.0AB5
Task 4: Configure
the violation action to block traffic from any additional MAC addresses and log
the violation.
For this purpose we
need to configure violation action to restrict. In restrict mode, the packet is
dropped and a log is generated when the violation occurs.
SW1(config-if)#switchport
port-security violation restrict
SW1(config-if)#exit
Task 5: Ping between
PC3 and PC4 to ensure they cannot communicate through SW1.
Traffic between PC3
and PC4 should not pass because the MAC address of PC3 is not configured
statically, and the limit of three MAC addresses is already reached with one
from PC1, one from PC2, and one from SW2.
PC3:\>ping 192.168.1.4
Pinging 192.168.1.4 with 32 bytes of
data:
Request timed out.
Request timed out.
Request timed out.
Request timed out.
Now try pinging from
PC1 to PC4.
PC1:\>ping
192.168.1.4
Pinging 192.168.1.4
with 32 bytes of data:
Request times out.
Reply from 192.168.1.4: bytes=32 time<1ms TTL=127
Reply from 192.168.1.4: bytes=32 time<1ms TTL=127
Reply from 192.168.1.4: bytes=32 time<1ms TTL=127
Now exit
configuration mode and save the configuration.
SW1(config)#end
SW1#write memory
Packet Tracer File
Clicking this button will begin the download of a ZIP file. Inside the ZIP file, you'll find a Packet Tracer Activity (.pka) file, which will automatically track your progress as you configure the network.

